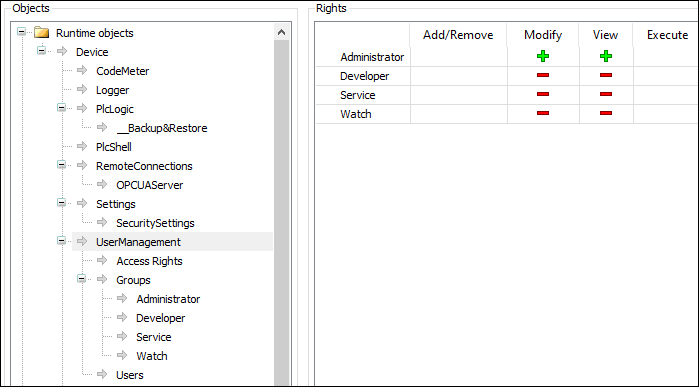
Tab: Access Rights
Recommendations for data protection
In order to minimize the risk of data security violations, we recommend the following organizational and technical actions for the system where your applications are running. Whenever possible, avoid exposing the PLC and control networks to open networks and the Internet. Use additional data link layers for protection, such as VPN for remote access, and install firewall mechanisms. Restrict access to authorized persons only, change any existing default passwords during the initial commissioning, and change them in regular intervals.
Important
Detailed information on the concept and use of device user management is provided in the Handling of Device User Management chapter.
There you will also find the following instructions on how to use the editor:
First-time login to the controller for editing and viewing its user management
Setting up a new user in the user management of the controller
Changing of access rights to controller objects in the user management of the controller
Loading user management from a *.dum file, modifying it, and downloading it to the controller in offline mode
On this tab, you define the device access rights of device users to objects on the controller. As in the project user management, users must be members of at least one user group and only user groups can be granted certain access rights.
The Show access rights page option has to be selected in the CODESYS options in Device editor category.
Note that this CODESYS option can be overwritten by the device description.
A component for the user management has to be available on the controller. That is the primary requirement.
Users and user groups have to be configured on the Users and Groups tab.
Toolbar of the tab
| Switches on and off the synchronization between the editor and the user management on the device. If the button is not "pressed", then the editor is blank or it contains a configuration that you loaded from the hard disk. When you enable the synchronization while the editor contains a user configuration that is not synchronized with the device yet, you are prompted what should happen to the editor contents. Options:
|
|
|
|
|
Device user | User name of the user currently logged in on the device |
In the tree structure, the objects are listed to which actions can be executed at runtime. The objects are each assigned by their object source and partially sorted in object groups. In the Rights view, you can configure the access options for a user group to a selected object. |
. Object source (root node)
A description of the objects is located in the Overview of the objects table. |
Object groups and objects (indented) Example: Device with child nodes Logger, PlcLogic, Settings, UserManagement. |
In general, the subobjects inherit the permissions from the root object (Device or /). This means that if a permission of a user group is denied or explicitly granted to a parent object, then this first affects all child objects. The table applies for the object that is currently selected in the tree. For every user group, it shows the rights currently configured for the possible actions on this object. 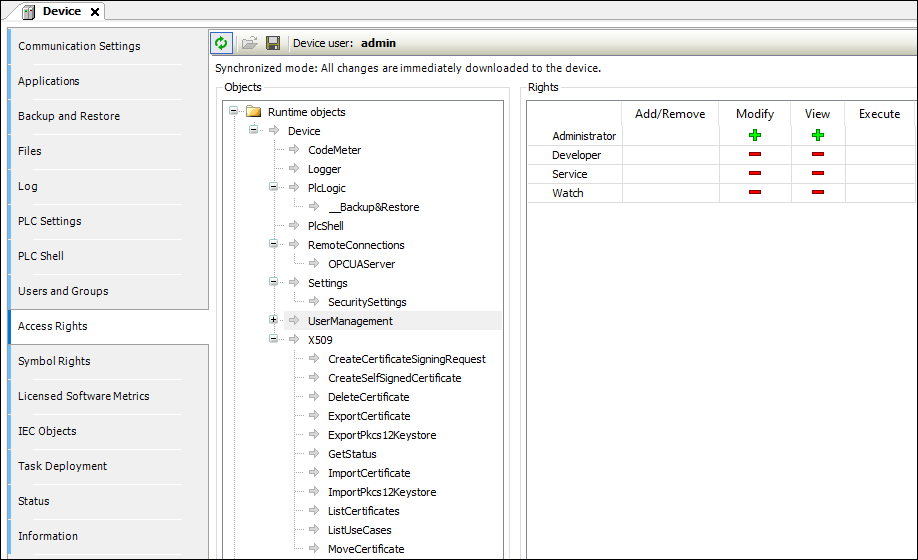 . Possible actions on the object:
| |
When an object is clicked, a table on the right side shows the access rights of the available user groups for the selected object. This allows you to quickly see:
. Meanings of the symbols
Change the permission by clicking the symbol. |
The Logger object on the Access Rights tab was created by the "Logger" component and controls its access rights. It is located directly below the Device runtime object.
The possible access rights for this object can be granted only for the View action.
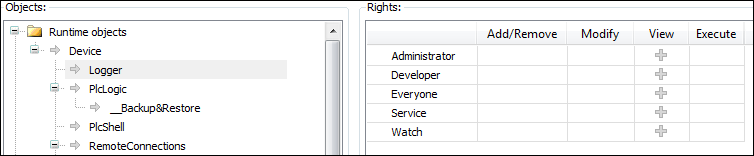
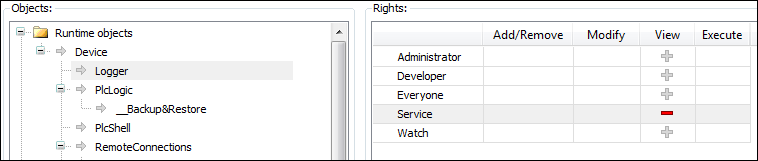
Initially, each object has a read access. This means that every user can read the "Logger" of a controller. If this access right should be denied for a single user group (Service in the example), then the read access to the logger object has to be denied explicitly.
Overview of the objects
| Online access to the logger is read only. Therefore, only the View access right can be granted or denied here. | ||||||
| All IEC applications are inserted here automatically as child objects during download. When an application is deleted, it is removed automatically. This allows specific control of online access to the application. Access rights can be assigned centrally over all applications in the PlcLogic The Administrator and Developer user groups have full access to the IEC applications. The Service and Watch user groups only have read access (for example for read-only monitoring of values). | ||||||
The following table shows which action is affected in particular when a specific access right is granted for an IEC application.
| |||||||
| Operation | Permission | |||||
Add/Remove | Execute | Modify | View | ||||
Login |
|
|
|
| |||
Create |
|
|
|
| |||
Create child object |
|
|
|
| |||
Delete |
|
|
|
| |||
Download / online change |
|
|
|
| |||
Create Boot Application |
|
|
|
| |||
Read variable |
|
|
|
| |||
Write Variable |
|
|
|
| |||
Force Variable |
|
|
|
| |||
Set and delete breakpoint |
|
|
|
| |||
Set Next Statement |
|
|
|
| |||
Read call stack |
|
|
|
| |||
Single Cycle |
|
|
|
| |||
Switch on flow control |
|
|
|
| |||
Start / Stop |
|
|
|
| |||
Reset |
|
|
|
| |||
Restore retain variables |
|
|
|
| |||
Save retain variables |
|
|
|
| |||
| Only the Modify permission is evaluated at this time. This means that only when the Modify permission has been granted to a user group can PLC shell commands also be evaluated. | ||||||
| Additional external connections to the controller can be configured below this node. Currently, access to the OPCUA server can be configured here. | ||||||
| This is the online access to the configuration settings of a controller.
| ||||||
| This is the online access to the user management of a controller. By default, read/write access is granted only to the administrator.
For more information, see: Handling of Device User Management | ||||||
| This controls the online access to the X.509 certificates. Two types of access are distinguished here:
Every operation is assigned to one of these two access rights. Each operation is inserted as a child object below X509. Therefore, access per operation can now be fine-tuned even more. | ||||||
All folders from the execution path of the controller are inserted below the "/" file system object. This allows you to grant specific rights to each folder of the file system. | |||||||